With the continuous improvement of people's health awareness and the upgrading of consumption concepts, products such as water purifiers and air purifiers have gradually moved from large construction sites to ordinary people's homes, becoming one of the secondary necessities of household consumption. These types of products are different from traditional household appliances. They mainly rely on frequently replaced accessories such as filters and filters to maintain their purification function, and their purification effect on pollutants is not visible to the naked eye, which is an important gap for many unscrupulous businesses to make profits.

At present, 70% of the water purifiers on the market mainly use RO reverse osmosis technology, usually using a 4-5 stage filtration method combining PP cotton, pre activated carbon, RO reverse osmosis membrane, and post activated carbon.
The working principle and filtration accuracy of each level of filter element are different, and the consumption progress will also vary depending on the source water quality and water usage value in different regions or even communities. Currently, most of the water purifier products on sale are sold by water purifier merchants who provide users with regular replacement services for each filter element, ranging from 6 to 36 months, through manual recording, or by placing a timer in the machine to remind users of the expiration of the filter element.
Manual door-to-door recording relies on a strong after-sales service system and accurate data transmission. Even traditional and well-established home appliance brands find it difficult to achieve timely and accurate results. The secondary pollution caused by the overdue service of the filter element is self-evident, while other businesses take advantage of consumer panic about water quality and frequently remind users to replace the filter element. Selling products at low prices, high-frequency filter cartridges, and manual door-to-door services to earn profits have become common tricks for many small water purifier manufacturers.
The huge profits in this type of consumables market have also made it a target for criminals to create counterfeits, leading to the emergence of: counterfeit goods rampant, seriously damaging brand reputation; Fake goods are difficult to distinguish between true and false, seizing the market for genuine products and damaging consumer interests; Directly leading to a decrease in consumer loyalty, directly affecting corporate interests, and disrupting the market landscape.
The application of Internet of Things technology has brought possibilities for product innovation, solving product anti-counterfeiting, distribution, and after-sales problems. However, the specific implementation of purification effects requires profound professional experience and vast industry data.
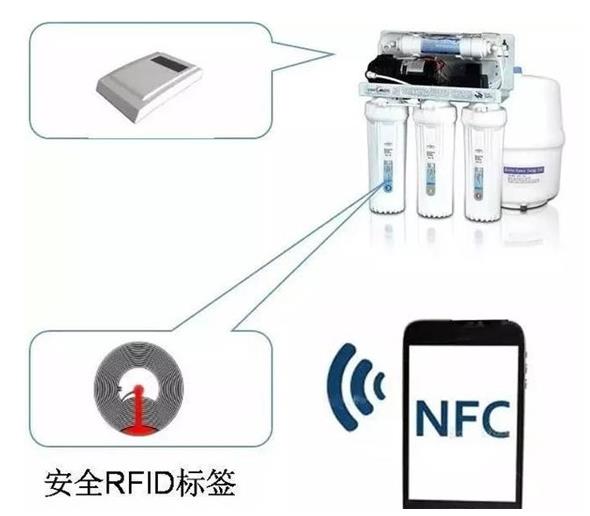
It is understood that many leading companies have started using RFID for product anti-counterfeiting, but universal RFID products are far from meeting the demand for anti-counterfeiting in the Chinese market:
UID anti-counterfeiting cloning has low difficulty and requires connection to the product database, making it impossible to achieve offline anti-counterfeiting
Once a single key encrypts data and the key is stolen, the loss is severe and the key is easily copied
Poor market control ability of enterprises
How to solve the above multiple problems? That's right, the focus that Little New is pushing today is the secure RFID tag chip!

Comparison and difference between universal RFID tag chips and secure RFID tag chips
Security chip carrier
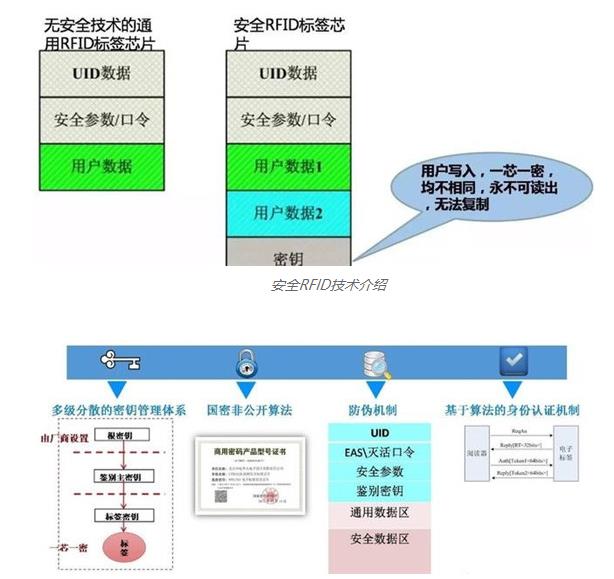
On the left is the traditional RFID tag chip structure diagram, which includes a UID+security password+user data, but there are security vulnerabilities.
On the right is the structure diagram of a password secure RFID tag chip. The biggest difference is that each tag has a key, which is written by the user, that is, the brand manufacturer. The key for each chip is different and cannot be read. By using authentication algorithms, the uniqueness of the label identity is determined to ensure that the label cannot be copied. The password security algorithm adds a security lock to RFID, and the key to this security lock is controlled by the manufacturer. Even the label chip supplier cannot crack and copy the label after the manufacturer issues the key. Brand manufacturers fully grasp the initiative of traceability.

Product features - Anti cloning (identity authentication)
Reader performs key based identity authentication on tags to achieve anti cloning
1. Reader's one-way identity authentication for tags (online)
2. Reader and tag bidirectional identity authentication (offline)
3. The authentication process does not transmit keys
Case One: Actual Application of Water Purifier

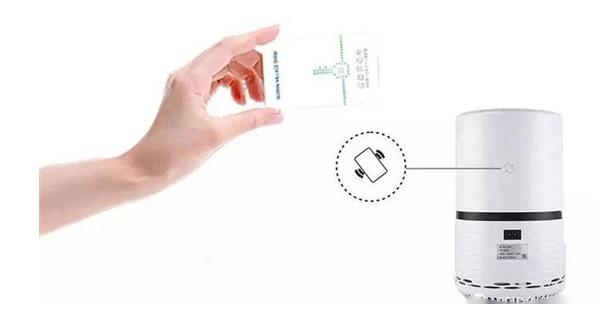
1. The reader is installed on the water purifier host
2. The electronic tag is installed on the filter element of the water purifier
3. When replacing the filter element, the host reader verifies the anti-counterfeiting of the filter element
(1) The identification of the filter element is true, the water purifier is working normally, and the working time of the filter element is recorded. According to the application market, users are reminded in a timely manner to replace the filter element
(2) Filter identification false, water purifier alarm, prompting users to replace genuine filter, ensuring user drinking water safety and water purifier operation safety
As ordinary consumers, NFC phones can be used to conduct online verification of filter cartridges, effectively protecting the rights and interests of ordinary consumers.
Scheme application mode

1. Utilizing an algorithmic bidirectional authentication mechanism, one core, one secret, and never readable, ensuring that RFID tags cannot be cloned
2. No need to connect to the backend database, easily achieve offline anti-counterfeiting identification, and complete filter cartridge anti-counterfeiting verification
3. The key to security and anti-counterfeiting solutions is in the hands of users, and even solution providers cannot clone them, reducing user application risks
Case 2: Actual application of printer toner cartridge management
As a huge market in daily life, consumer products play a crucial role in anti-counterfeiting, distribution management, or after-sales sales. By applying RFID to these links, product safety and quality can be improved, while also saving costs and helping to solve the two major problems in the retail industry: product stockouts and loss - products lost due to theft and supply chain disruptions. Taking printer toner cartridge management as an example:
1. The toner cartridge is equipped with an RFID tag, which is written into the authorized matching information by a dedicated card issuer
2. Install an RFID card reader on a specific part of the printer. When replacing the toner cartridge, only tags with built-in RFID authorization can be used, otherwise the printer will not function properly.
3. RFID tags have a unique UID and a large user data area, with independent management keys that can be used for item traceability and correct identification of specific providers. When a product malfunctions, it can also quickly seek after-sales service.
4. It can prevent suppliers or distributors from colluding with each other in different regions
5. Can protect and maintain the good integrity brand effect of the product